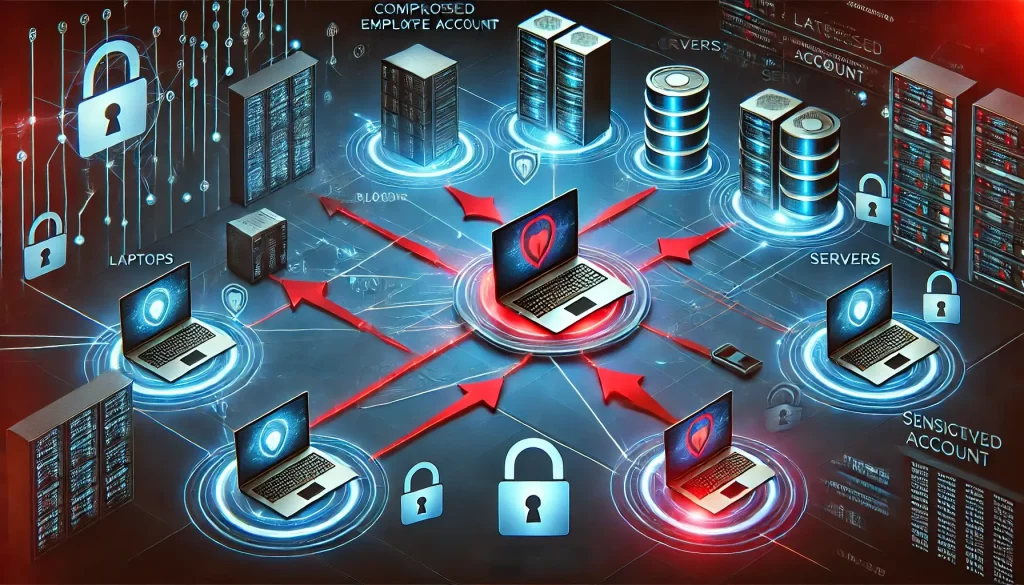
One of the most common attack vectors involves the compromise of employee accounts. Once an attacker gains access to an employee’s machine, they can execute lateral movements to access sensitive systems, escalate privileges, and cause widespread damage across the organization’s infrastructure.
This blog post will cover practical strategies to protect employee accounts from cyber threats, focusing on key techniques like penetration testing, vulnerability assessments, and employee security practices.
1. Understanding Lateral Movement and Its Risks
Lateral movement refers to the technique attackers use to move deeper into a network once they have breached an initial endpoint, such as an employee’s computer. By compromising one account, attackers can escalate privileges and access more critical systems, databases, and assets.
Key Risks from Lateral Movement:
- Data Exfiltration: Attackers gain access to sensitive data and intellectual property.
- Privilege Escalation: Gaining admin or root privileges allows complete control of systems.
- Destructive Actions: Malware can be deployed across the network, causing service outages or corruption of critical systems.
2. Penetration Testing: Simulating Real-World Attacks
Penetration testing (or “pen testing”) is one of the most effective ways to uncover weaknesses that attackers might exploit. This process involves authorized ethical hackers attempting to breach the organization’s defenses, simulating real-world attacks.
How Pen Testing Protects Employee Accounts:
- Simulates Phishing Attacks: Pen testers send phishing emails to test whether employees fall for credential theft tactics.
- Tests Endpoint Security: The testers examine if they can breach an employee’s device, then move laterally within the network.
- Privilege Escalation Checks: Testers attempt to elevate their access to administrator or root privileges to uncover vulnerabilities that allow privilege escalation.
Best Practices for Penetration Testing:
- Conduct regular penetration tests (quarterly or bi-annually).
- Use both internal and external pen testers to gain a broader view of vulnerabilities.
- Ensure that pen testing covers endpoints, network infrastructure, and cloud environments.
3. Regular Vulnerability Assessments: Closing Security Gaps
Vulnerability assessments are a proactive step organizations can take to identify, classify, and remediate weaknesses in their infrastructure before an attack occurs. While penetration testing simulates attacks, vulnerability assessments provide a continuous review of known vulnerabilities across systems.
Key Steps in Vulnerability Assessments:
- Asset Discovery: Identify all devices and systems connected to the organization’s network.
- Vulnerability Scanning: Use tools to scan systems for unpatched software, misconfigurations, and outdated security settings.
- Prioritization: Rank vulnerabilities based on their severity and potential impact on the organization.
- Remediation: Patch software, update configurations, and strengthen access controls to close security gaps.
Regular vulnerability assessments ensure that weak points are discovered and mitigated before attackers have a chance to exploit them.
4. Securing Employee Accounts: Practical Steps for Defense
While pen testing and vulnerability assessments help secure infrastructure, protecting employee accounts involves implementing specific security measures focused on user behavior, access control, and monitoring.
a. Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to verify their identity through multiple channels (e.g., SMS, email, or authentication apps) before accessing accounts. Even if an attacker compromises an employee’s password, they cannot access the account without the second authentication factor.
- Use MFA for all critical systems, including email, VPNs, and internal systems.
- Implement app-based authenticators like Google Authenticator or Microsoft Authenticator for stronger security over SMS-based authentication.
b. Least Privilege Principle
Enforcing the principle of least privilege ensures that employees only have access to the systems and data necessary for their job functions. This limits the damage an attacker can cause if they compromise an employee’s account.
- Regularly audit user permissions and remove unnecessary privileges.
- Segment networks to restrict lateral movement if one endpoint is compromised.
c. Endpoint Detection and Response (EDR) Solutions
EDR tools monitor endpoint activity and detect suspicious behavior that could indicate an attack. By analyzing processes, file changes, and network connections, EDR systems can detect and block lateral movements in real time.
- Implement EDR tools across all employee devices, both on-premises and remote.
- Use EDR to detect malware, anomalous user activity, and lateral movement attempts.
d. Employee Cybersecurity Training
Employees are often the first line of defense. Regular training programs can teach employees how to spot phishing emails, avoid downloading malicious software, and follow secure practices when accessing sensitive data.
- Conduct regular phishing simulations to test employee response.
- Provide clear guidelines on how to report suspicious activity or potential security breaches.
5. Monitoring and Incident Response: Detecting and Mitigating Attacks Early
Effective monitoring and incident response capabilities are essential to detect threats before they escalate. By continuously monitoring employee account activity and having a well-defined incident response plan in place, organizations can minimize damage.
a. Network Monitoring and Anomaly Detection
Monitor network traffic for unusual patterns, such as large data transfers, unauthorized access attempts, or unexpected privilege escalation activities. Advanced Security Information and Event Management (SIEM) systems can correlate these anomalies to identify potential breaches.
b. Incident Response Plan
Develop a comprehensive incident response plan that outlines the steps to take when a breach occurs. This should include:
- Isolating compromised accounts and devices to prevent further lateral movement.
- Forensic analysis to understand how the attacker gained access.
- Patching vulnerabilities and reviewing affected systems to prevent future attacks.
c. Security Audits and Continuous Monitoring
Schedule regular security audits to ensure that all employee devices comply with the latest security policies and standards. Continuous monitoring allows for real-time detection of suspicious behavior and rapid response to potential threats.
6. Zero Trust Architecture: Assuming Breach to Protect Critical Systems
A Zero Trust security model assumes that no user or device, whether inside or outside the network, can be trusted by default. This model emphasizes:
- Verifying the identity of all users and devices before granting access.
- Continuously monitoring for malicious activity.
- Applying micro-segmentation to limit the scope of any breach.
Adopting a Zero Trust architecture greatly reduces the risk of attackers moving laterally within the network after breaching an employee account.
Conclusion
Organizations must adopt a multi-layered security approach to protect their employees’ accounts from cyber threats.
Penetration testing, vulnerability assessments, strong access controls, and continuous monitoring are essential strategies. Additionally, regular employee training and the implementation of robust endpoint detection solutions can significantly reduce the risk of account compromise and lateral movement.
By following these practical steps, businesses can stay one step ahead of cybercriminals and safeguard their infrastructure from devastating breaches.