With countless devices and users connected to networks at all times, ensuring that sensitive data remains secure is a top priority.
Yet, despite advancements in cybersecurity, many users unknowingly expose themselves to risks—especially when using public networks without encryption.
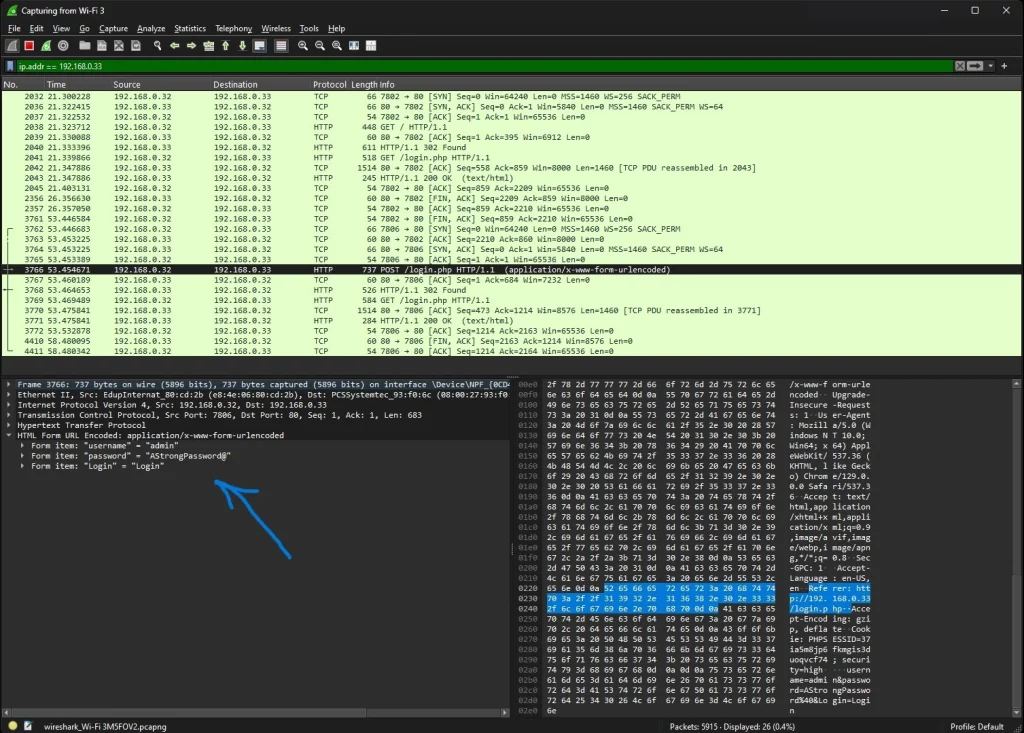
Wireshark, one of the most popular and powerful packet analyzers, can easily capture and display traffic on a network, revealing the vulnerabilities of unencrypted data.
In this article, we will explore Wireshark’s capabilities, understand how unencrypted traffic can be captured, and dive into a real-life story to demonstrate how these risks play out. We’ll also discuss best practices for protecting yourself on public networks.
What is Wireshark?
Wireshark is an open-source packet analyzer that allows users to capture and interact with data traveling across a network in real-time.
It breaks down the captured traffic into readable packets, allowing network administrators, cybersecurity professionals, and even hackers to study the traffic patterns, identify potential vulnerabilities, and troubleshoot network issues.
Key Features of Wireshark:
- Packet Capture: Wireshark can intercept and log traffic that flows through a network.
- Deep Packet Inspection: It can break down network communication into detailed packet-level views, which display the protocols, source/destination addresses, and the data being transferred.
- Real-time Monitoring: It can capture live traffic as it happens and present it to users for real-time analysis.
- Open Source and Multi-Platform: Wireshark is free to use, open-source, and available on multiple platforms including Windows, macOS, and Linux.
How Unencrypted Traffic is Captured and Read in Wireshark
Imagine you’re connected to a public Wi-Fi network at a coffee shop or an airport.
If the website or service you’re interacting with doesn’t encrypt its traffic (using HTTPS or a VPN), anyone on the same network—including someone using Wireshark—can easily sniff the data you send and receive.
Here’s how this works:
- Shared Network Access: When devices are on the same network, they send data through shared channels. For example, public Wi-Fi hotspots or unsecured routers typically have minimal segregation between users. A malicious actor can join the same network, positioning themselves to capture traffic with Wireshark.
- Packet Sniffing: Wireshark captures data packets as they travel across the network. In the case of unencrypted communication, these packets can be easily interpreted because they are not obscured by encryption. This means sensitive information such as:
- Login credentials (usernames and passwords)
- Messages
- Browsing activity
- Emails can be intercepted and read.
- Reconstructing Data: Once Wireshark captures these packets, it can reorganize the raw packet data into meaningful streams. If the communication is unencrypted, you can view the entire content of a message, file transfer, or login session.
Example of Capturing Unencrypted HTTP Traffic:
To illustrate, let’s say you’re visiting a website that uses HTTP (instead of HTTPS). An attacker with Wireshark can filter captured packets by HTTP protocol, allowing them to see the exact web pages you visit, extract form data (like login credentials), and monitor your online activity.
Because HTTP transmits data in plain text, the attacker doesn’t need to decrypt the information.
Real-Life Example: The Starbucks Wi-Fi Incident
In 2018, a cybersecurity researcher discovered a serious vulnerability while sitting at a Starbucks coffee shop. Using Wireshark, he demonstrated how easy it was to capture unencrypted traffic on the public Wi-Fi network.
What Happened?
As customers connected to Starbucks’ free Wi-Fi, the researcher began capturing network traffic using Wireshark. Because many users were browsing websites that didn’t enforce HTTPS or using apps with poor security practices, he was able to capture:
- Unencrypted login credentials for social media accounts.
- Personal emails sent over unencrypted connections.
- Sensitive search queries that people assumed were private.
One particular instance highlighted the dangers of public Wi-Fi. The researcher noticed a user logging into their bank account, but the bank’s website wasn’t properly configured to use HTTPS across all pages.
As a result, the customer’s username and password were sent in plaintext, which the researcher could easily see. This level of exposure is especially dangerous because anyone with bad intentions could use that information for identity theft or fraud.
The incident sparked discussions about the inherent risks of using public Wi-Fi without proper security measures.
The Risks of Public Networks: Why Encryption Matters
Public Wi-Fi networks, such as those found in cafes, airports, and hotels, are a hacker’s paradise.
Since they often lack robust encryption, they provide an ideal environment for attackers to intercept sensitive data.
Connecting to these networks without using encryption tools like VPNs (Virtual Private Networks) or accessing encrypted websites (HTTPS) opens the door to potential privacy breaches.
Here’s why encryption is crucial:
- Data Protection: Encryption scrambles the data you send and receive, so even if someone captures the traffic, they can’t make sense of it without the decryption key.
- Secure Communication: Encryption ensures that sensitive communications, like financial transactions or login credentials, remain private and cannot be intercepted.
- Public Network Safety: VPNs, in particular, create a secure, encrypted tunnel between your device and the internet, preventing anyone on the same network from snooping on your activities.
Protecting Yourself: Best Practices for Safe Network Usage
- Use Encrypted Websites (HTTPS): Always ensure that websites you visit use HTTPS, indicated by a padlock symbol in the browser. This encrypts the communication between your browser and the website.
- Use a VPN on Public Networks: A VPN encrypts all the traffic from your device, making it difficult for attackers to capture or interpret your data.
- Disable File Sharing: When connected to a public network, ensure that file sharing is turned off, as it can expose your files to others on the same network.
- Use Two-Factor Authentication (2FA): If your login credentials are compromised, 2FA provides an additional layer of security, preventing unauthorized access to your accounts.
- Monitor Network for Unusual Activity: If you’re responsible for a network, tools like Wireshark can help you monitor traffic for signs of intrusion or data theft.
Conclusion: Wireshark, Public Networks, and the Importance of Encryption
Wireshark is a powerful tool that can help professionals diagnose and solve network issues, but it also highlights the risks associated with unencrypted traffic.
Whether you’re a cybersecurity professional or just an everyday internet user, understanding how easily unencrypted data can be captured and read by someone using a tool like Wireshark is crucial to protecting yourself online.
As the Starbucks incident shows, your private information is never truly safe on a public network unless you take the right precautions.
Whether you’re using a VPN, ensuring HTTPS connections, or following other best practices, the key takeaway is simple: Always encrypt your data to keep it secure.





