Securing sensitive data and monitoring file integrity across enterprise networks is essential. Integrating Wazuh, a robust SIEM solution, with VirusTotal, a powerful threat intelligence platform, adds a layer of security.
This guide will walk you through integrating VirusTotal’s API with Wazuh’s File Integrity Monitoring (FIM) module to automatically scan and flag potential malware threats when file changes are detected in real-time.
Initial Requirements
Before we dive into the integration steps, ensure the following are in place:
- A working Wazuh SIEM setup (Wazuh Manager and Agent installed)
- Wazuh Agent successfully connected to the Wazuh Manager
- A VirusTotal API key (obtainable from VirusTotal)
How Wazuh Works With VirusTotal
Wazuh’s File Integrity Monitoring (FIM) module allows us to track changes to specific files or directories, such as file additions, deletions, and modifications.
Normally, FIM scans occur based on a predefined schedule, but we’ll set up real-time monitoring for this integration.
Once a file change is detected in a designated directory, Wazuh triggers an alert. The file hash is automatically extracted and sent to VirusTotal via their API for analysis.
VirusTotal will check the file’s hash against its database of known malware, providing insights on whether the file poses any risk.
Step-by-Step Guide to Integration
Step 1: Obtain a VirusTotal API Key
To start, you need an API key from VirusTotal:
- Go to VirusTotal.
- Create an account and navigate to your profile section.
- Click on the API Key and copy your unique API key. This key is essential for allowing Wazuh to communicate with VirusTotal.
Step 2: Configure Wazuh to Integrate VirusTotal
Now, it’s time to configure the Wazuh Manager to send alerts and file hashes to VirusTotal:
- On the Wazuh Manager server, open the configuration file located at
/var/ossec/etc/ossec.conf - Add the following snippet, replacing
API_KEYwith the VirusTotal API key you obtained in Step 1:
<integration>
<name>virustotal</name>
<api_key>API_KEY</api_key>
<group>syscheck</group>
<alert_format>json</alert_format>
</integration>
- Save the file and restart the Wazuh Manager for the changes to take effect:
systemctl restart wazuh-managerStep 3: Set Up Wazuh Agent for Real-Time Monitoring
On the Wazuh Agent side, we will configure real-time monitoring for a specific directory. Here’s how to do it:
- On the agent machine, open the Wazuh configuration file located at
/var/ossec/etc/ossec.conf - Add the following snippet to monitor a directory (e.g.,
/home/john) in real-time:
<syscheck>
<directories check_all="yes" realtime="yes">/home/john</directories>
</syscheck>
- Restart the Wazuh Agent to apply the changes:
systemctl restart wazuh-agentStep 4: Test the Setup by Downloading a Malicious File
For testing purposes, we will download a known malicious file into the directory we just set up for monitoring.
Warning: This step should only be performed in a controlled and isolated environment. Downloading and extracting malicious files can lead to security issues.
- Navigate to the DasMalwerk (https://das-malwerk.herokuapp.com) site, which hosts various malicious files for research purposes. (this website will alert your browser, proceed with caution)
- Use
wgetorcurlto download a sample malicious file into the monitored directory:
wget <link_of_the_malicious_file> -P /home/john- Unzip the file:
unzip <maliciousfile.zip>
# Note: The password for malicious files on DasMalwerk is "infected".
Step 5: Monitor Wazuh for File Integrity Changes
Once the malicious file is downloaded and extracted, Wazuh’s FIM will immediately detect the new and modified files. You can view these changes in the Wazuh Dashboard:
- Go to Modules > Integrity Monitoring.
- You should see both the
.zipfile and the extracted contents being tracked in real time.
Step 6: VirusTotal Scan and Response
After detecting a file integrity event, Wazuh automatically sends the file hash to VirusTotal for analysis. VirusTotal will compare the hash against its massive repository of malware.
If the file is known to be malicious, VirusTotal will return a detailed report that you can view directly from the Wazuh Dashboard.
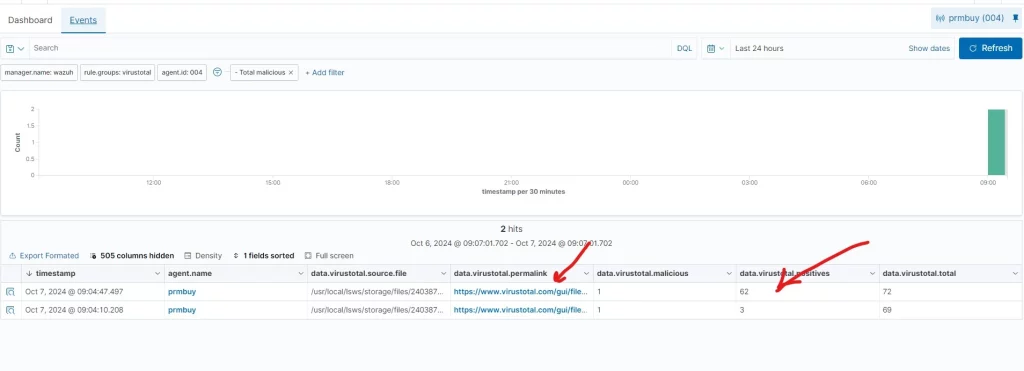
Important Notes
- Isolated Environment: Always perform this activity in an isolated environment. Never download or extract potentially malicious files on production systems.
- Passive Detection: This integration is primarily for detection. It does not remove or mitigate the malicious actions that might be triggered by the malware. Further actions, such as containment and remediation, will need to be handled manually or through additional automated response mechanisms in Wazuh.
Conclusion
By integrating Wazuh with VirusTotal, you enhance your security posture by enabling real-time malware detection through file integrity monitoring.
This combination allows for quick identification of suspicious files and automated analysis via VirusTotal’s extensive malware database.
With the flexibility of Wazuh’s SIEM capabilities and the intelligence of VirusTotal, you can better protect your environment from evolving threats.
This integration exemplifies how open-source tools can work together to provide enterprise-grade security solutions.





